Workflows
Hamsa, a Layer 2 EVM-compatible Unified Confidential Ledger, leverages enhanced Polygon and zero-knowledge proof cryptography for secure, auditable enterprise transactions in private or consortium networks.
B2B Transfer Workflow Example
The figure below presents a B2B transfer end-to-end workflow and module interactions for a representative business transaction within the proposed privacy-preserving pipeline.
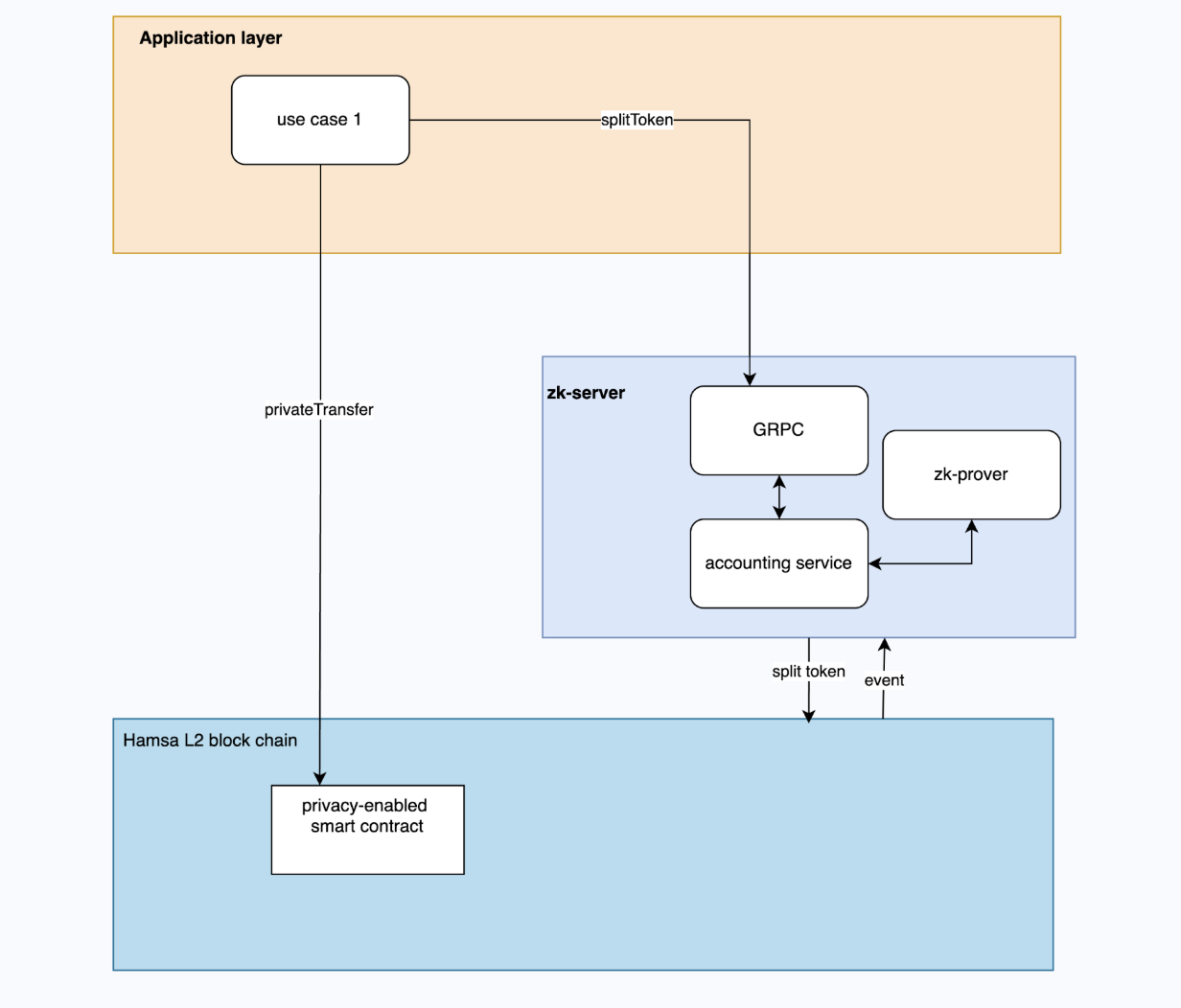
Workflow and module interaction.
User A calls and GRPC endpoint GenerateSplitToken to split his balance. The accounting service first calls zk-prover to generate the ZK proof needed for splitting a new token. It then calls the privateSplitToken of the smart contract to create the token on chain
The smart contract on-chain will verify the ZK-proof first and execute additional validations before storing the new token on-chain. It emits an event after everything is completed successfully.
When the accounting service receives the on-chain event, we say the reservation is done. Notice at this moment, user A’s balance is still not changed.
The User A can consume the split token in any business workflows (e.g. java backend, another smart contract) by calling theprivateTransfer function of the smart contract.
Updated 6 months ago
